As you can imagine, the last couple of years have seen us get a lot more enquiries from clients looking to stress-test their crisis preparedness. Cyber incidents are especially tricky to handle, for a number of reasons:
- The information vacuum is more acute and extended
It can take a while – days, potentially – for the facts of the incident to be established, but the shock and concern amongst those potentially affected ramps up as quickly as any other incident-driven crisis. - Mobilizing the internal team is more complex
Depending on the nature of the incident, there can be an especially wide range of internal colleagues to involve, from technical staff to HR, legal to regulator, investor relations to media relations. - Scenario-planning is trickier and understanding – let alone communicating – the risks involved is harder
Explaining the nature of the vulnerability that has been exploited is a challenge, compounded by hypotheticals and best/worst case assumptions with few known facts.
Over the last year we’ve seen a number of emerging and growing trends in real-world cyber incidents which clients are starting to use in their own resilience planning:
Stronger regulatory muscle
Last year, we saw average fines levied by the UK regulator for data breaches double to £146,000, while in the US firms such as Anthem and Uber settled large cases in the tens of hundreds of millions of dollars. The reality is that regulators are getting tougher around the world, backed up by more clear-cut expectations enshrined in law – such as the requirement in Europe to notify the authorities within 72 hours of the discovery of a personal data breach. Prepare your templates in peacetime, and think ahead of time about when you’ll disclose.
State-sponsored attacks and 0days
Hacker groups such as The Lazarus Group, believed to be aligned to the North Korean state, have gone after cash targets such as payment systems and bank networks; whereas other state-sponsored attacks have had espionage as the mission, as Marriott found to its cost. The threats emerging from undisclosed vulnerabilities (‘zero days’) are some of the most difficult to guard against, and the geopolitical scale to these attacks obviously dwarfs the resources of all but the largest corporations. The best defence is likely to be in preparation and training users to be intelligent users of technology: ultimately, it was a spearphishing attack targeted at an employee that enabled malware to be installed which affected Chile’s national ATM network.
Risks exposed by mergers and acquisitions
As IT becomes the business, not just enables it, cyber due diligence becomes ever more important. Systems integration naturally introduces the complexity of more servers in more datacenters, with more suppliers and more users involved. While the task of auditing and securing those digital empires is one for IT, there’s a resilience task to make sure the teams managing them have oversight of what there is and who is supporting and maintaining them so vulnerabilities don’t simply emerge from oversights. In a nutshell: it might be a server you inherited, but when it’s breached for want of a software patch, customers will blame the brand they recognise.
Reliance on 3rd parties in the digital supply chain
British Airways revealed the loss of almost 400,000 customers’ payment information when third party code on their online booking portal was compromised. It highlighted the challenge of modern web sites, which aren’t simply pages of content, but are composed of layers of advertising tracking scripts, third party shopping carts, and libraries that make the rich web experience we expect these days. As with state-sponsored attacks, third party infrastructure is hard to secure definitively, so the resilience task has to be ensure that your monitoring and testing regime, and links to partners in the supply chain – are strong so that you can respond quickly if code is compromised.
Shifting perceptions of what constitutes “fair use” of data
Facebook found to its cost that you don’t necessarily need to lose your users’ data to get the blame (though they’ve done that too). Convoluted data-sharing regimes which flout the spirit of the moral contract users believe they have with you can be enough to spark regulatory enquiries, fines, class action suits and customer boycott campaigns. There’s signs of a shift in perceptions of what ‘fair’ looks like as firms start to get more creative/manipulative in their use of data and users react by choosing services and tools which enable them to encrypt, delete, or block unwanted snooping. Communication has an important role to play here in being clear and frank with people about the basis on which a digital service is being offered, and how their data is used. Transparency build trust, while the drip-drip of revelations about a business model which needlessly infringes privacy can destroy it.
A cyber incident can be managed and trust restored, but lose trust with customers about your fundamental way of operating, and the damage runs much deeper – into your very licence to operate.
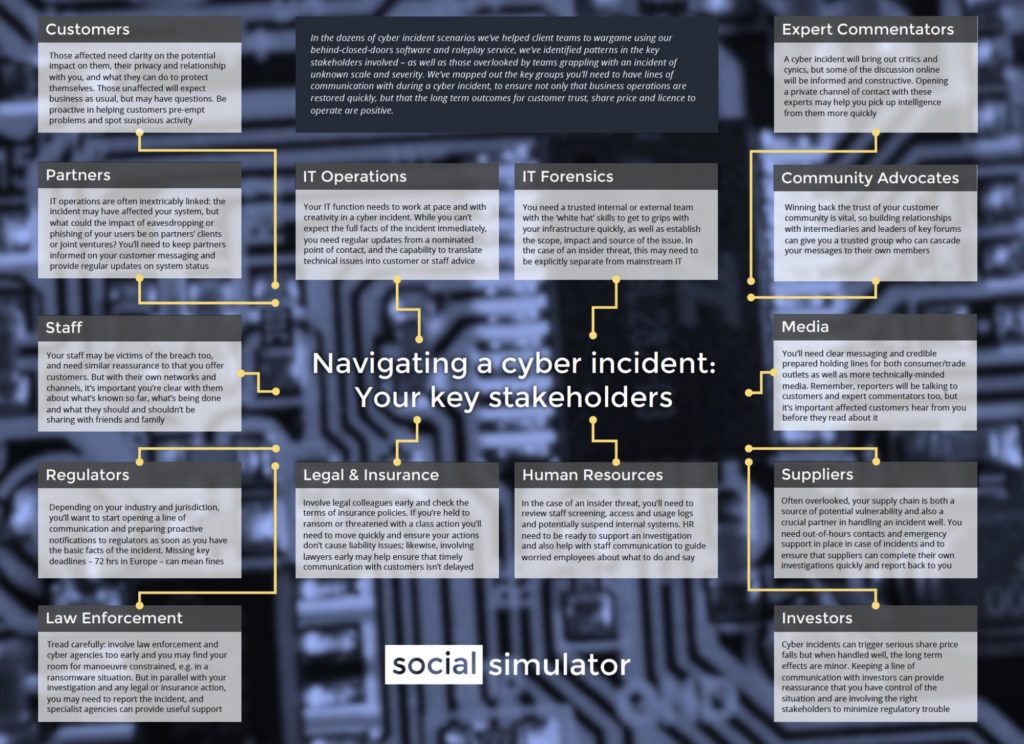
Your cyber incident stakeholders
In the dozens of cyber incident scenarios we’ve helped client teams to wargame using our behind-closed-doors software and roleplay service, we’ve identified patterns in the key stakeholders involved – as well as those overlooked by teams grappling with an incident of unknown scale and severity. We’ve mapped out the key groups you’ll need to have lines of communication with during a cyber incident, to ensure not only that business operations are restored quickly, but that the long term outcomes for customer trust, share price and licence to operate are positive. Take a look at our infographic, and let us know what you think.